With cryptocurrencies, you can execute transactions directly without the need for traditional financial institutions as intermediaries. Although decentralization is at the core of Blockchain technology, it’s vulnerable to several attacks. Chief among them is the 51% Attack. In this article, we’ll take you through what a 51% Attack is, its outcomes, and several real-world examples. We’ll also take a peek at how 51% Attacks can be nullified and the future of Blockchain security. Stay tuned.
Understanding a 51% Attack
So, how does a 51% Attack work? A 51% Attack happens when a group or entity gains illegitimate control of over half of a Blockchain’s computational or mining power. In a typical Proof of Work (PoW) system, mining power simply refers to the network’s ability to interpret cryptic puzzles that secure and validate transactions. When an attacker holds over 50% of this power, they can tweak the entire Blockchain network in diverse harmful ways.
The Outcome of an Attack
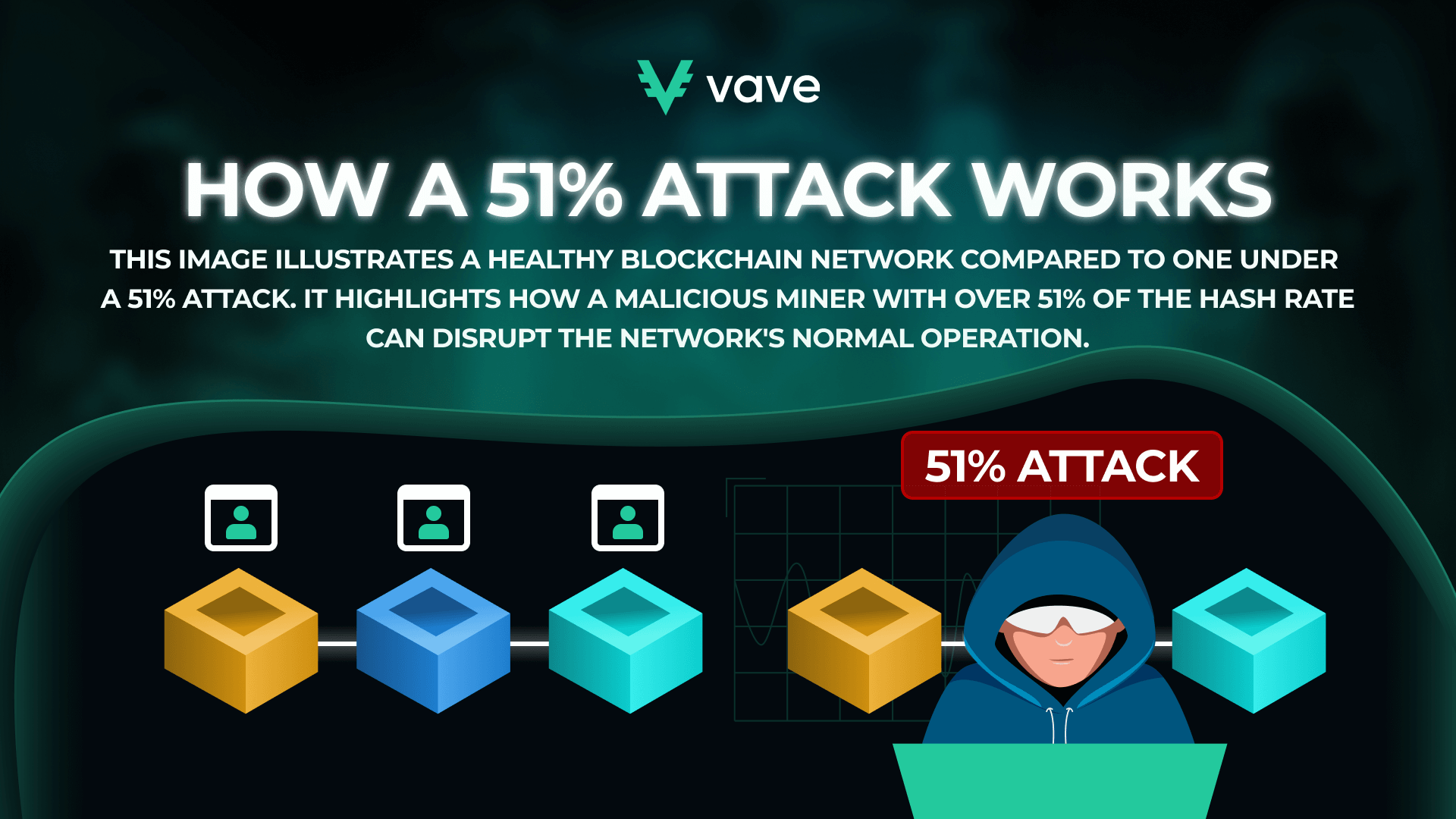
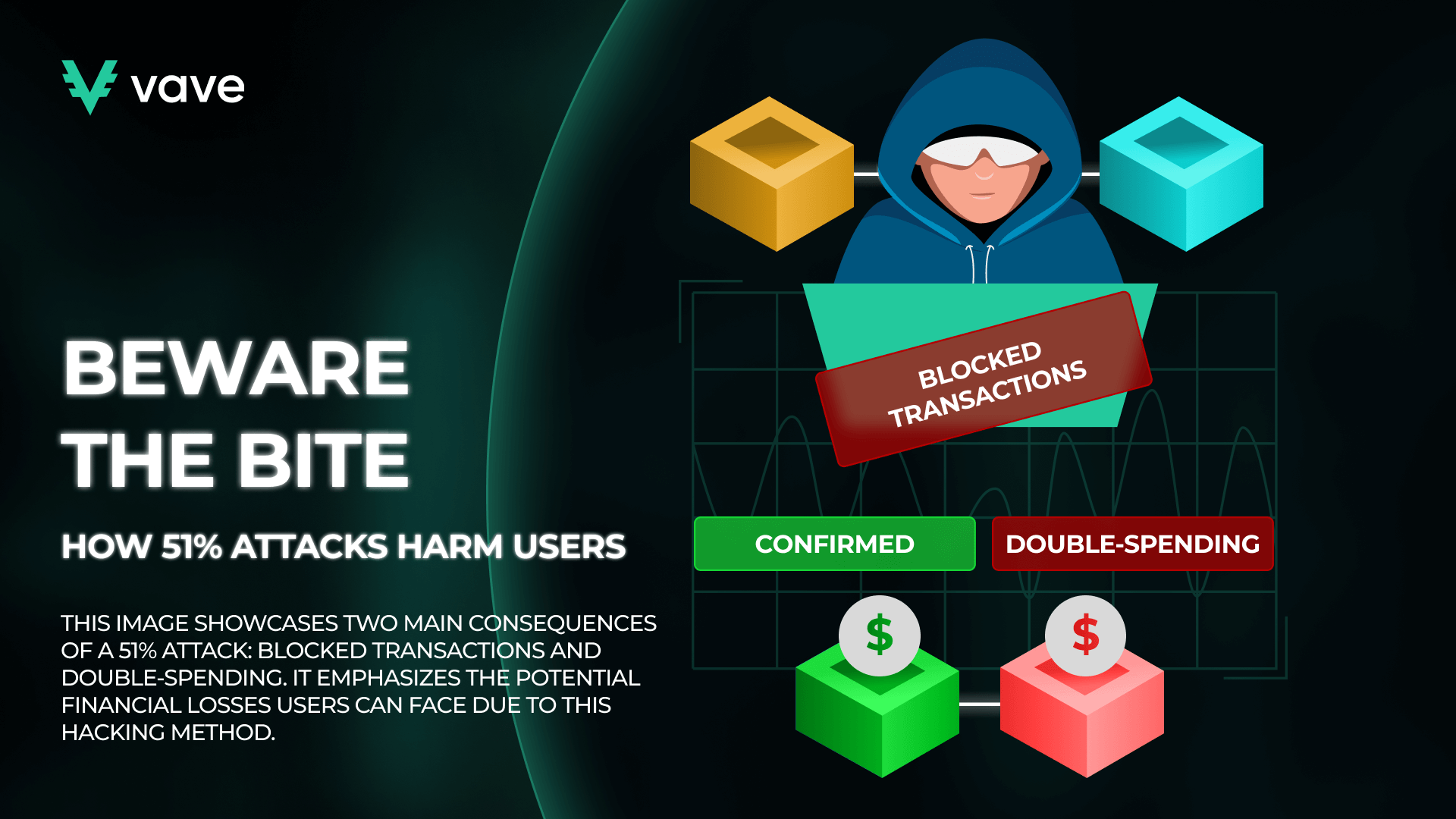
Attacks can affect a cryptocurrency network and associated users. Here’s how:
Double-Spending
One of the most harmful effects of a 51% Attack revolves around double-spending. When a transaction is confirmed and added to the Blockchain, it’s unchangeable and irreversible. However, when an attacker gains access to more than 50% of a network, they can create a version of the Blockchain where that payment is non-existent.
This scenario allows them to spend the amount of coins featured in that transaction once more on the regular chain. When double-spending occurs, it undermines the principle of digital scarcity, which is critical for the valuation of cryptocurrencies.
Blocking Transactions
One of the other risks of 51% Attack in crypto is transaction blocking or censorship. When an attacker gains substantial control over a crypto network, they can easily void transactions. This means that they can decide what payments get confirmed and those that won’t.
Typically, transaction blockades in 51% Attacks target specific groups or individuals. As such, their accounts can be frozen, rendering the network unusable for them. In more critical scenarios, the attacker can restrict all payments on that network.
Who Is at Risk?
If you’re new to the 51% Attack topic, one thing you’d like to know straightaway is what cryptocurrencies can be affected. As such, you might even be making Google queries along the lines of “can Bitcoin be vulnerable to a 51% Attack?” Quickly, let’s see what crypto networks are susceptible to 51% Attacks.
The first thing to note is that not all cryptocurrencies can withstand a 51% Attack. Revered and highly valued cryptocurrencies like Bitcoin and Ethereum rarely experience these attacks. Why? An astronomical amount of computational power is required to control more than half of their networks. However, smaller cryptocurrencies are more vulnerable to 51% attacks due to their relatively lower hash rates.
Real-World Examples of Successful 51% Attacks
Since the Blockchain became a concept, there have been several real-world examples of 51% Attacks, including:
- Bitcoin Gold (BTG): Back in May 2018, BTG experienced a 51% Attack. This attack allowed the infiltrator to double-spend BTG tokens to the tune of over $18 million. This singular scenario saw the cryptocurrency’s market value and reputation fall drastically.
- Vertcoin (VTC): In December 2018, VTC was the victim of a 51% Attack. Once again, the attacker double-spent 603 VTCs (an estimated $100,000).
- Ethereum Classic (ETC): In August 2020, ETC suffered a 51% Attack. The attacker had the luxury of double-spending ETCs valued at $5.6 million.
Likelihood of the Attack
The possibility of a 51% Attack occurring depends solely on the security and scale of a cryptocurrency network. Cryptocurrencies like BTC and ETH aren’t prone to 51% Attacks, as they’ve got larger Blockchain networks. However, lesser-known and smaller cryptos with a few miners and low hash rates are more susceptible to 51% Attacks.
Advancements in technology have led to cryptocurrencies adopting rock-solid security add-ons. As such, the Blockchain is almost impregnable. However, a select percentage of the crypto community remains concerned about the possibility of a 51% Attack. Therefore, efforts have been made to develop consensus algorithms and increase the scale of decentralized networks. Why? To reduce the chances of a 51% Attack.
Summarily, although the possibility of a 51% Attack is drastically low nowadays, it can actually occur. As such, if you’re looking to learn how to diversify your crypto portfolio, set sail with the best cryptocurrencies to avoid 51% Attacks. Notable mentions include Bitcoin, Ethereum, Bitcoin Cash, and Litecoin.
How to Prevent a 51% Attack
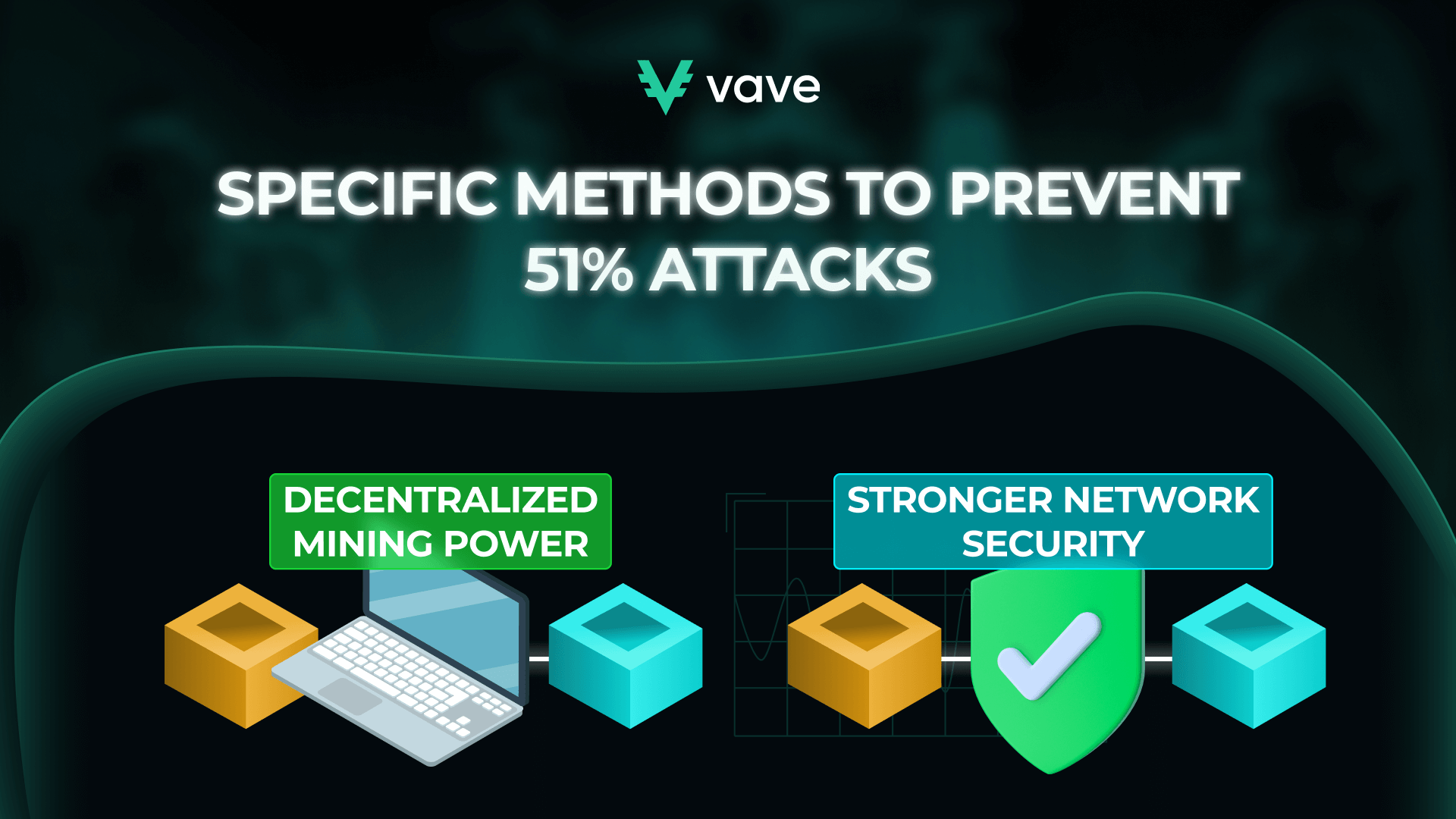
Learning how to protect yourself from a 51% attack is no mean feat. Preventing these attacks requires a diverse approach that emphasizes technology-driven solutions and community engagement. Thankfully, several strategies can prevent these attacks.
The Power of Decentralization: Mitigating 51% Attacks
An effective way to stop 51% of attacks on the entire blockchain is to ensure high levels of decentralization. Mining power shouldn’t be focused in one place but shared among numerous participants or nodes. When this happens, it becomes extremely difficult for an entity to generate the computational power required for 51% of Attacks.
Several Blockchain networks have incorporated additional safety measures to enhance security. These safeguards (i.e., hybrid consensus mechanisms) join PoW together with other algorithms, such as Proof of Stake (PoS). PoS-themed systems are important as they reduce the likelihood of 51% Attacks. They require that all validators have a financial stake within the cryptocurrency network. Why? It’ll suit their long-term interests in security.
The Future of Blockchain Security: Addressing 51% Attack Threats
Blockchain technology is constantly evolving. As such, it’s important to nip the possibility of 51% Attacks in the bud. That way, decentralized networks will become more sustainable in the long run. We’ve seen the development of several mechanisms, such as energy-efficient algorithms and shearing. These innovations can restrict 51% Attacks from ever occurring and tarnishing the image of cryptocurrencies.
Furthermore, education and awareness themed around the relevance of decentralization are vital to the growth and adoption of cryptocurrency. Besides 51% Attacks, cryptocurrency users will receive materials on securing their Blockchain trail. As such, we expect how to secure your crypto wallet and other guides to take precedence in the cryptocurrency sphere soon.
Conclusion
In this 51% Attack explained article, you’ve seen that these activities pose a great threat to cryptocurrencies and their users. When these attacks take center stage, users can be barred from making transactions. Additionally, payments can be nullified and tweaked. These outcomes can lead to the devaluation and ultimate crash of a cryptocurrency.
But it isn’t all doom and gloom. With the promotion of decentralization and the development of innovative security addons, these attacks can become non-existent in the future. However, for these scenarios to take place, the cryptocurrency community must work together. That way, it’ll weather any storm thrown against it.
FAQ
What Is the Difference Between PoW and PoS?
Can Small Cryptocurrencies Defend Against 51% Attacks?


















